By Elisa Bertacin
Faced with the “challenge of transmitting messages or communications accessible to the limited few, “Cryptography” has proven to be a concept that has always fascinated man. Cryptography is that science which aims to provide an instrument capable of keeping secret all information that is not for public disclosure.
The operation with which information is hidden is referred to as encryption. To encrypt information, an algorithm (cipher) is used. The message that is to be encrypted is referred to as plaintext, which, through the use of a key, is converted into the encrypted text or the ciphertext.
Decryption, on the other hand, is the reverse process for which a ciphertext is converted into plaintext through the use of the key to the encryption.
Throughout history, encryption methods have prevalently been used by four categories of people: the military, diplomats, diarists, and lovers. Given the context provided by the paper, it is obvious that the first two are what interest us the most, and in particular the military.
In his time, Plutarch spoke of the Spartan generals, who sent and received coded messages using the scytale, a small cylinder of wood. The message was written on a thin strip of parchment wrapped around the scytale. The decryption of the message was possible only with a cylinder of the same diameter upon which the parchment would be wrapped to reveal the message.
Cryptography, even among the Roman emperors, was widely used for communications of strategic importance; one of the oldest known ciphers is the so called “Caesar cipher”, or shift cipher. It was normal, for example, that Augustus wrote his messages substituting each letter with the one that followed, while Julius Caesar substituted each letter with the letter that was three positions down the alphabet. These are clearly very simple techniques and fall into the general category of substitution ciphers. These ciphers, however, are easily cracked the moment that all that is needed to crack the encryption is frequency analysis, or the study of the linguistic statistics of the language used to write the plaintext (i.e. studying which are the most recurrent letters and bigrams, or the most infrequently used in a given language) and the subsequent substitution of these letters with the most frequently recurring in the ciphertext. If the substitution ciphers keep the original order of the units of plaintext, transposition ciphers, on the other hand, alter the order of the letters without however substituting each letter for another (as is the case for the Spartan scytale). In the event of a columnar transposition, the key must be a word or a phrase that doesn’t contain repeated letters; the plaintext is laid out along rows that are the same length as the key; the vertical columns that are thus created are then numbered, starting with the letter below the letter in the key that is closest to the beginning of the alphabet, and so on for the rest of the letters of the key. The ciphered text will be read in columns, starting with the column of the lowest number. Although this is a more complex encryption method than the substitution cypher, this too may be deciphered. In fact, all one has to do is figure out what the length of the key is – a feasible task especially in the event that the presence of certain specific words are present in the plaintext – and the attempt to put the columns in order.
The most famous cipher machine ever to have been built was the Enigma machine used in the Second World War by the German armed forces. Although it was being constantly altered and improved, a group of experts, among which Marian Rajewski and Alan Turing, were able to crack it and speed the decryption process, thus guaranteeing strategically vital information to the Allied Forces.
With the advent of the computer era, cryptoanalysis has become even more important. The techniques used are essentially still based on the same ideas as traditional (substitution and transposition) cryptography, even though the level of complexity is significantly greater. The difference being, that today, the tendency is to use such complex cryptographic algorithms that, even if the cryptoanalyst had enormous quantities of encrypted text s/he would still not be able to decipher the text.
In fact, in a moment in time in which daily life, both public and private, is becoming more and more computerised, the ability to protect one’s privacy and personal data is an increasingly relevant issue. Just think of all of the credit card transactions which are recorded in a database, or all of the phone calls that are recorded by the telephone companies to extract market data, or all of the emails that we send and receive on a daily basis. Aside from the legal measures established to protect the right to privacy (with all of its limits and attached criticisms), cryptography represents a particularly valid instrument for protecting one’s data, regardless of the fact that this science (or art) is still seen to be inaccessible and exclusive to military spheres.
There are two instances in daily life where cryptography is necessary:
- The case in which the information, once encrypted, must simply be kept safe on site. In this case, the primary problem is to render it invulnerable to someone with unauthorised access.
- The case in which the information must be transmitted. The problem consists in preventing the information from being understood in the event it should be intercepted (the typical example being an exchange of emails). It is this case that is the most problematic today and which draws the attention of the encryption software companies. Take electronic mail, for instance: it circulates the Internet, travelling the world over – and the Internet in and of itself constitutes a channel for communication that in no way guarantees the confidentiality of the data in circulation – and before it reaches its destination, it must often travel through different nodes. The greater the number of nodes that the message travels through, the greater the possibility that the message will be intercepted or tampered with. With the power that modern calculators have today, in fact, these last are not only capable of using filters to capture only the data that is targeted but are able to modify the data and do so in the moment that the message is being passed from the sender to the recipient and all without being detected.
One fundamental rule of modern cryptography is the assumption that the cryptoanalyst is aware of which general cryptographic method is being applied. Therefore, the primary element becomes the key. For some algorithms, the key used in the encryption and decryption is one and the same, while for others it varies. One may distinguish between the following:
– symmetric key algorithms (also referred to as secret key or single key), which allow the sender and recipient to use the same key to encrypt or decrypt a message. This key is used as a parameter for a unidirectional and reversible function; because of this, the recipient can alter the encryption by applying the reverse function and the same key that the sender used.
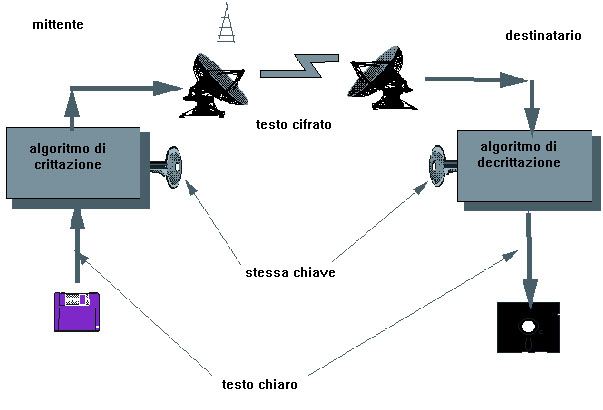
This method is based on the ability of the sender and recipient to keep the key a secret.
The first major symmetrical algorithm used in computerised cryptography was the Data Encryption Standard (DES). DES was developed in the United States in the 1970s to run with a 56-bit key (meaning that there are roughly 70 quadrillion possible combinations). With the ever changing and developing IT world, however, DES has since been declared no longer secure and has been substituted by the Advanced Encryption Standard (AES), which uses 128-, 192-, or 256-bit keys.
Symmetrical key systems may be used to increase levels of confidentiality (in other words, to protect information from being seen by unauthorised users) and the integrity of the information (by preventing the information from being modified or manipulated in any way), and boasts user authentication capabilities as well. However, this type of encryption is not free from problems from the moment that the transmission of the key to the two users is sent via telephone, with all of its related risks. Moreover, it is not possible for the sender or the receiver to prove to a third party that a message was effectively produced by either of the two.
– asymmetric key algorithms (also referred to as public key). The concept of asymmetric cryptography was introduced in 1976 by Whitfield Diffie and Martin Hellman. The two thought to capitalise on the use of two keys, creating a method that was essentially based on two concepts: on one hand, a message that is encrypted with one of the two keys may be decoded only with the other key; on the other hand, it is not mathematically possible to extract one key from the other. Each user on the web shares their own public key, while keeping the other secret. The copy of keys is based on a prime number system, which makes it potentially very secure given the infinite availability of prime numbers and hence an infinite number of possible combinations. The relatively well-known cryptographic programme, Pretty Good Privacy (PGP), allows practically every type of message and data to be encrypted and it is applied most to electronic mail systems. Once a message has been encrypted by the sender, no one other than the recipient will be able to read the message, not even the sender.
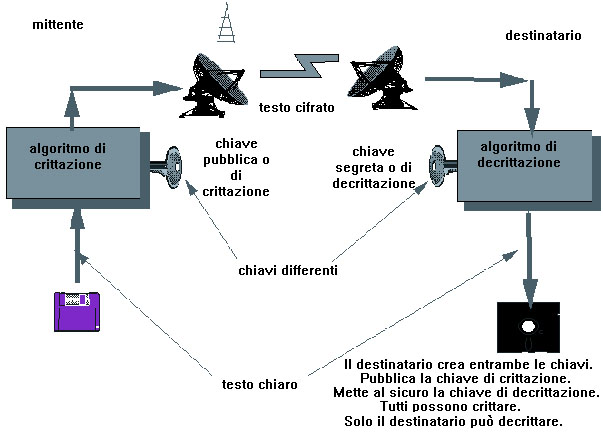 Other than the sender, it is possible for the content of the message to be authenticated by applying a hash function to the text; a one-way hash function transforms a normal text of arbitrary length into a string of limited length. This represents the only “digital signature” of the message, referred to as the hash value or the cryptographic checksum. If the message gets altered, this value will also change.
Other than the sender, it is possible for the content of the message to be authenticated by applying a hash function to the text; a one-way hash function transforms a normal text of arbitrary length into a string of limited length. This represents the only “digital signature” of the message, referred to as the hash value or the cryptographic checksum. If the message gets altered, this value will also change.
It is clear that asymmetrical algorithms resolve the issue for which the exchange of secret keys could be intercepted. This is due to the fact that with these algorithms all one needs to do is to send the public key to the corresponding user. Nevertheless, not even this type of cryptography is free of weak points or immune to criticism. In fact, it is for this reason that today there is a general tendency to use both types of cryptographic algorithms. The asymmetrical systems are particularly slow, and for this reason, when large volumes of data must be encrypted, the symmetrical one-key system is to be preferred.
